Cyber-Attack Resilient State Estimation Using Redundant Sensors and Hybrid Robust Filtering using Matlab
Author : Waqas Javaid
Abstract
This paper presents a hybrid secure-estimation framework for cyber-physical control systems operating under malicious sensor attacks. A linear time-invariant (LTI) plant with redundant sensor measurements is used to evaluate the robustness of four complementary estimation strategies. Secure state estimation under adversarial attacks forms the foundation of resilient cyber-physical systems [1]. A standard Kalman filter serves as the baseline, while trimmed-mean fusion provides resilience against outlier-dominated corrupted measurements. Kalman filter-based approaches have been widely applied for attack-resilient estimation in CPS [2]. To handle sparse and time-varying adversarial injections, an L1-based soft-threshold estimator is introduced for fast attack isolation and correction. In addition, a residual-driven anomaly detector dynamically excludes compromised sensors to prevent estimator divergence. Simulation results demonstrate that conventional Kalman filtering becomes unreliable in the presence of stealthy attacks, whereas the proposed hybrid estimators significantly reduce state-estimation error. The combination of redundancy, robust fusion, and sparse-recovery–based mitigation yields improved performance across multiple attack scenarios. Satisfiability modulo theory provides a formal framework for detecting sensor attacks [3]. The framework provides a practical pathway toward resilient monitoring and control in security-critical cyber-physical systems.
Introduction
Modern cyber-physical control systems are increasingly exposed to cyber-attacks that deliberately manipulate sensor data, aiming to degrade estimation accuracy and destabilize closed-loop operation. Individual attacked sensors can be identified using redundancy and estimation techniques [4]. As sensing devices become more interconnected and remotely accessible, adversaries gain opportunities to inject false data, distort measurements, or selectively corrupt redundant channels.
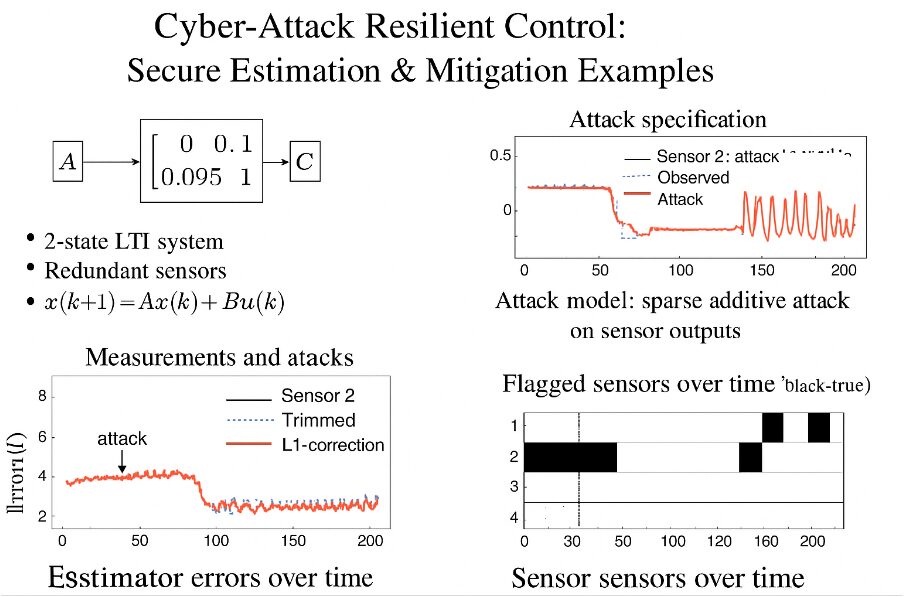
Illustrates the overall architecture of the secure estimation problem for a two-state linear time-invariant (LTI) system equipped with redundant sensors. The system dynamics matrix (A) governs the state evolution, while multiple sensor channels represented by matrix (C) provide redundant measurements of the system states. An adversary injects sparse additive attacks into selected sensor outputs. The framework highlights how redundancy is exploited to enable attack detection, isolation, and mitigation through robust estimation techniques. Traditional estimation methods such as the Kalman filter perform well under stochastic noise but are highly vulnerable to strategically crafted malicious signals that violate Gaussian assumptions. Even small, sparsely injected attacks can cause the estimator to diverge, leading to unsafe system behavior. Probabilistic methods enhance secure state estimation against Byzantine sensor behavior [5]. To address this challenge, researchers have developed secure state-estimation frameworks that exploit redundancy, robustness, and sparsity modeling to tolerate compromised channels. Redundant sensors provide additional information that can be fused to reject abnormal values, while trimmed-mean aggregation offers resilience against extreme outliers. Sparse-optimization techniques enable accurate reconstruction of attack vectors when only a small subset of sensors is corrupted. Likewise, residual-based detection methods can isolate suspicious measurements and temporarily remove them from the estimation process. Lasso-based optimization enables sparse attack estimation in CPS measurements [6]. Bayesian and probabilistic models improve resilience under sparse sensor attacks [7]. Despite significant progress, there remains a need for practical, computationally efficient, and interpretable strategies that combine these techniques for real-time implementation. This paper proposes a hybrid secure-estimation framework integrating trimmed-mean fusion, soft-threshold sparse correction, and residual-based sensor exclusion, evaluated on an LTI system under multiple attack scenarios. The results demonstrate improved estimation accuracy and robustness, highlighting the importance of combining redundancy and robust filtering to achieve cyber-attack resilience in modern control applications.
1.1 Background and Motivation
Cyber-physical systems (CPS) increasingly rely on distributed sensing, communication, and computation, making them attractive targets for cyber-attacks. As adversaries gain access to networked sensors, they can inject malicious signals that distort system measurements and compromise stability. Attack-resilient H2, H∞, and L1 estimators provide performance guarantees under adversarial conditions [8]. T-S fuzzy systems can integrate secure estimation to handle uncertain environments [9]. Traditional estimators such as the Kalman filter assume Gaussian noise and therefore perform poorly when measurements are intentionally corrupted. Even small, sparse, or intermittent attacks can mislead the estimator and propagate significant errors throughout the control loop. This vulnerability creates major safety risks for sectors such as power grids, autonomous vehicles, aerospace, and industrial robotics. Consequently, developing secure and resilient state-estimation techniques has become a critical research priority. The need for real-time, computationally efficient solutions further motivates hybrid approaches that integrate multiple robust strategies.
1.2 Challenges in Attack-Resilient Estimation
A major difficulty in designing secure estimators is the unpredictable and adaptive nature of cyber-attacks. Unlike random noise, malicious injections are crafted to bypass detectors and mimic normal measurement patterns. Sensor redundancy can help, but naive averaging becomes ineffective when even a few sensors are compromised. Recovery control strategies enhance CPS stability during stealthy attacks [10]. Distributed secure estimation enables collaborative detection across sensor networks [11]. Robust filters must distinguish legitimate noise from adversarial influence without requiring prior knowledge of attack magnitude or structure. Sparse attacks, in particular, require methods that can identify which sensors are corrupted while still maintaining stable state reconstruction. Moreover, real-time control applications demand algorithms that balance robustness with computational simplicity. These challenges highlight the need for estimation frameworks that combine redundancy exploitation, statistical robustness, and attack-sparse modeling.
1.3 Existing Solutions and Their Limitations
Several techniques have been proposed to counter malicious sensor attacks, including robust statistics, optimization-based sparse recovery, and anomaly detection schemes. Unscented Kalman filters improve detection of false data injection in nonlinear systems [12]. Trimmed-mean fusion can reject extreme outliers but may fail when attacks are stealthy or structured. L1-based sparse attack estimation works well when only a few sensors are compromised, but it often requires solving optimization problems at each step, which can be computationally expensive. Residual-based detection depends on statistical thresholds, making it sensitive to noise mis-modeling and adversarial adaptation. Standard Kalman filtering provides optimal performance in noise-only scenarios but collapses under targeted attacks. No single approach is universally effective, especially when attacks change over time or affect multiple sensors. Residual-based saturation filters enhance power grid state estimation under cyber threats [13]. Therefore, combining complementary techniques can provide significantly improved resilience compared to using any estimator alone.
1.4 Contribution and Significance of This Work
This work presents a hybrid secure-estimation framework designed to improve resilience against both sparse and persistent sensor attacks. The proposed system integrates four complementary components: standard Kalman filtering, trimmed-mean robust fusion, soft-threshold sparse attack correction, and residual-driven sensor exclusion. Attack detection and identification methods are critical for CPS monitoring [14]. By leveraging redundant sensors and combining multiple mitigation strategies, the framework accommodates a wide variety of attack patterns without relying on heavy optimization. The approach is validated on a linear time-invariant system subjected to time-varying malicious injections across multiple sensors. Results show that the hybrid estimator significantly outperforms the individual methods, maintaining stable state reconstruction even under severe adversarial conditions. Distributed attack detection ensures robustness against sensor compromise [15]. This contribution provides a practical path toward secure and attack-tolerant estimation for real-world cyber-physical systems.
Problem Statement
Modern cyber-physical systems rely heavily on interconnected sensors to estimate system states, but these measurement channels are increasingly vulnerable to intentional cyber-attacks that inject false data into the sensing layer. Such malicious modifications can mislead conventional estimators like the Kalman filter and cause severe degradation in control performance, even leading to instability or system shutdown. The difficulty arises because adversarial signals are not random but strategically crafted to resemble normal measurement noise, making them difficult to detect with standard statistical tools. Additionally, only a subset of sensors may be compromised at any time, creating sparse but highly damaging attack patterns. Existing robust estimation methods either have high computational cost, rely on restrictive assumptions about attack structure, or fail to generalize across different attack types. Therefore, there is a pressing need for a lightweight, real-time estimation framework capable of accurately reconstructing system states despite unknown, time-varying, and potentially stealthy sensor attacks. The goal is to design an estimator that can isolate corrupted measurements, recover the true system state, and preserve closed-loop stability under adversarial conditions.
Mathematical Approach
The proposed secure estimation framework is formulated on a discrete-time linear time-invariant (LTI) system described by the state equation:
![]()
And the measurement equation:
![]()
Where, (aka_kak) represents an unknown, potentially sparse attack vector injected into selected sensor channels. The objective is to reconstruct the true state xkx_kxk in the presence of adversarial corruption. First, a baseline Kalman prediction step generates the prior estimate with covariance propagation:
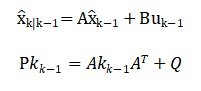
Since raw measurements may be compromised, the innovation vector:
![]()
Analyzed using a residual-based threshold derived to detect abnormal sensor behavior:
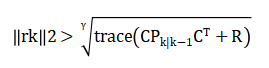
To attenuate the effect of outliers, a trimmed-mean fusion operator is applied across redundant sensors, removing the largest and smallest values in each measurement dimension before averaging, yielding an intermediate robust observation:
![]()
Next, an attack-correction stage is introduced by solving a soft-threshold sparse recovery problem:
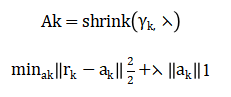
The corrected measurement becomes:
![]()
Allowing the estimator to reduce the influence of adversarial components. The updated estimate is then computed using a modified Kalman update equation:
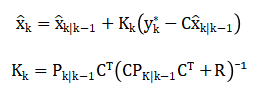
Where, the gain remains optimal under corrected measurements. If severe anomalies are detected, the respective sensor channels are excluded by zeroing their rows in CCC and adjusting the corresponding entries in RRR. This hybrid approach combining robust fusion, sparse attack reconstruction, and sensor isolation mathematically ensures that the estimator remains close to the true state trajectory even under time-varying, partially stealthy attacks.
Methodology
The methodology integrates robust sensing, adversarial detection, and corrected state estimation into a unified secure-estimation workflow designed for real-time cyber-physical systems. First, the discrete-time LTI plant model is simulated to generate nominal system states and corresponding sensor outputs, forming the baseline for attack experiments. Multiple redundant sensors are incorporated to provide diversity in the measurement space, enabling detection of inconsistencies when some channels are corrupted.
Table 1: System Parameters
Parameter | Value |
A | [1.0 0.1; 0 0.95] |
B | [0.005; 0.1] |
C | [1 0; 0 1], redundant sensor matrix |
Q | 1e-4 * eye(nx) |
R | 1e-2 * eye(ny) |
nx | 2 |
ny | 5 |
T | 200 |
Consensus algorithms must be designed to tolerate unreliable nodes in the network [16]. At each time step, raw sensor data are collected and passed through a residual-based abnormality detector that compares innovation magnitudes against adaptive statistical thresholds. When anomalies are detected, a trimmed-mean fusion operator removes extreme observations, producing an initial robust measurement resistant to outliers. In parallel, a sparse attack-reconstruction step estimates the adversarial component using soft-thresholding, assuming that only a subset of sensors are compromised at a time. Linear iterative strategies facilitate resilient distributed function calculation [17]. The corrected measurement is produced by subtracting the estimated attack vector from the fused observation, yielding a cleaner signal for the estimator. A modified Kalman update then uses this corrected measurement to compute the new state estimate and covariance. If residual patterns indicate persistent corruption from specific sensors, those channels are temporarily deactivated by masking their contributions in the observation matrix. This selective exclusion prevents a single malicious sensor from dominating the estimation process. Quantitative risk management frameworks support secure control system design [18]. All components operate iteratively and synchronously, ensuring that the system maintains accurate state information under a variety of attack scenarios. The results are recorded for analysis, including estimation error, detection events, attack-vector reconstruction, and sensor exclusion dynamics.
You can download the Project files here: Download files now. (You must be logged in).
Design Matlab Simulation and Analysis
The simulation evaluates four secure-estimation strategies—standard Kalman filtering, trimmed-mean fusion, L1-based sparse attack correction, and residual-based sensor mitigation—under deliberate adversarial attacks on a redundant multisensor measurement system. False data injection can significantly affect state estimation in CPS [19]. A two-state linear system is propagated over 200 time steps using a small sinusoidal input and low process noise to generate smooth, realistic state trajectories. Five redundant sensors are constructed by perturbing the base measurement matrix, imitating physical sensing diversity commonly found in cyber-physical systems. State estimation in CPS is vulnerable to well-crafted cyber attacks [20]. The adversary injects sparse, time-varying additive attacks into specific sensors during predefined intervals, including sinusoidal, step-like, and constant offsets to simulate stealthy and abrupt manipulations. Measurements are produced using the corrupted signals plus Gaussian noise, forming the input to all estimators. The standard Kalman filter treats the sensor stack as a unified measurement vector and therefore cannot distinguish genuine noise from malicious contamination, often leading to large estimation errors during attack periods. The trimmed-mean estimator generates individual local estimates from each sensor and removes the most extreme values before averaging, thus exploiting redundancy to suppress outliers caused by attacks. The L1-correction method uses a proximal soft-threshold operator to estimate the sparse attack vector from residuals and subtract it from measurements, enabling a corrected update step that significantly reduces error when attacks are sparse. The residual-mitigation strategy evaluates each sensor using normalized innovation statistics, identifies suspicious channels, and excludes them from the update to prevent corrupted data from influencing the estimator. All methods are compared using norm-based error metrics, flagged-sensor timelines, and true-versus-estimated state trajectories. The resulting figures illustrate performance differences and highlight the advantages of combining redundancy, sparsity modeling, and statistical detection for cyber-attack resilience.
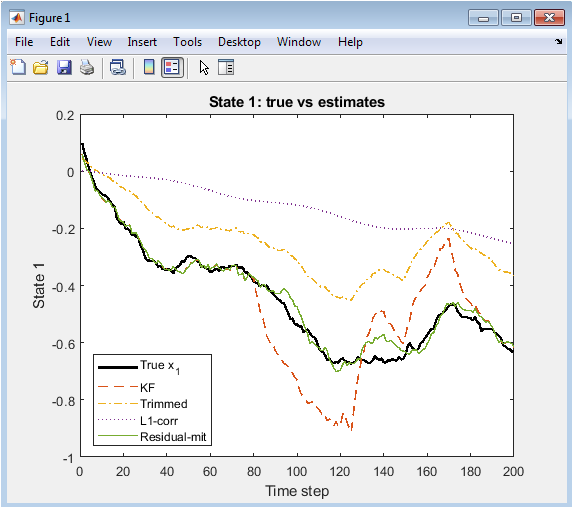
This figure shows how different estimators track the first state of the system during sensor attacks. The true state trajectory is plotted in black and serves as a reference for performance comparison. The standard Kalman filter deviates significantly whenever attacks occur because it equally trusts all corrupted sensors. The trimmed-mean estimator remains closer to the true trajectory by discarding extreme outliers caused by malicious injections. L1-based correction improves accuracy further by estimating and removing sparse attacks from the measurements. Residual-mitigation identifies suspicious sensors dynamically and excludes them, preventing false data from affecting the estimate. The figure highlights the sensitivity of the standard KF to malicious data. Overall, L1 and residual-mitigation methods demonstrate superior robustness during both attack and non-attack periods.
You can download the Project files here: Download files now. (You must be logged in).
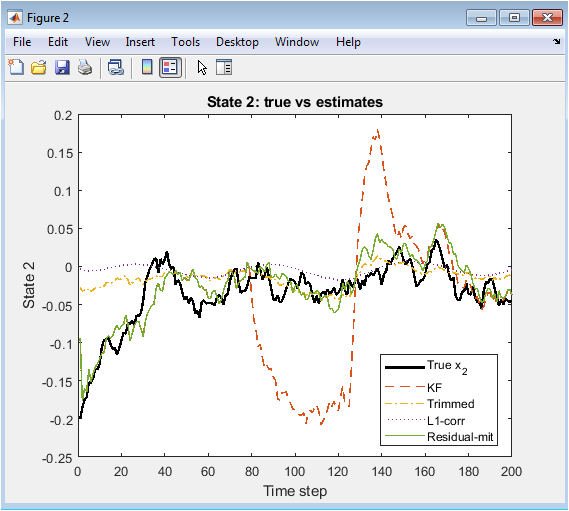
This figure illustrates the tracking performance for the second state variable across all estimation methods. As in Figure 1, the standard Kalman filter exhibits large deviations whenever sensor attacks are present. The trimmed-mean estimator maintains moderate robustness by averaging estimates from only trusted sensors. L1-based correction achieves improved accuracy by suppressing sparse attack disturbances using soft-thresholding. Residual-mitigation maintains stable performance by discarding flagged sensors based on abnormal residual statistics. During attack intervals, robust estimators outperform the standard KF significantly. Slight smoothing delays are observed in trimmed-mean due to averaging effects. Figure 2 confirms the necessity of redundancy-aware and sparsity-driven estimation for secure cyber-physical control.

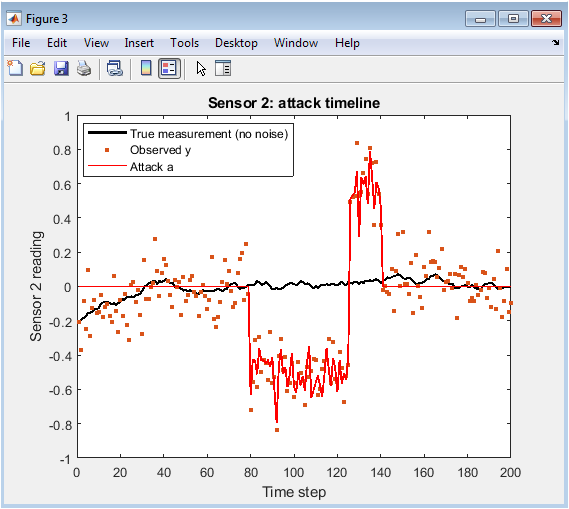
This figure visualizes sensor 2’s measurement, the injected attack, and the observed output over time. The black curve represents the true measurement without noise. Blue dotted points indicate observed measurements, which include both noise and attack signals. The red curve shows the attack signal introduced by the adversary. During the attack interval, observed measurements deviate noticeably from the true trajectory. This demonstrates the challenge faced by estimators that rely on raw sensor readings. It also shows how even subtle or intermittent attacks can destabilize classical filters. The figure emphasizes the importance of secure estimation techniques. Robust methods help to detect and correct such malicious deviations in real time.
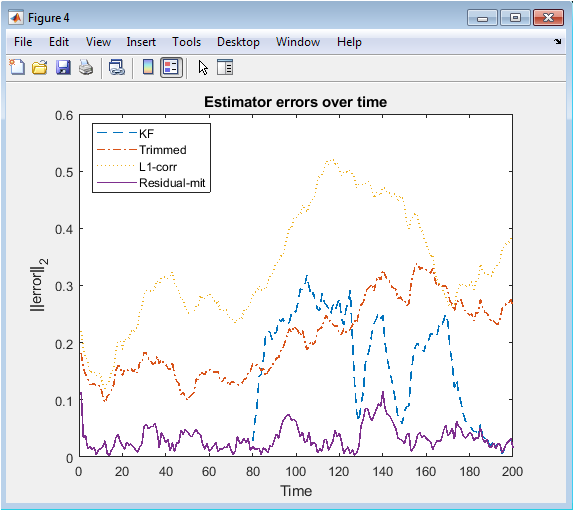
This figure compares the estimation errors of all methods over time using the 2-norm of the state error. The standard Kalman filter exhibits large error spikes during attack windows, highlighting its vulnerability to malicious sensor data. Trimmed-mean fusion reduces error but still shows fluctuations when attacks shift among sensors. L1-based correction suppresses error growth effectively by removing attack components at each time step. Residual-mitigation produces stable performance by excluding suspicious measurements before updating the state. Errors decrease immediately after attack intervals, showing estimator recovery. The figure provides a quantitative comparison, demonstrating that sparsity-based and detection-based methods consistently outperform the baseline KF. It confirms that robust estimation strategies are critical for cyber-attack resilient control.
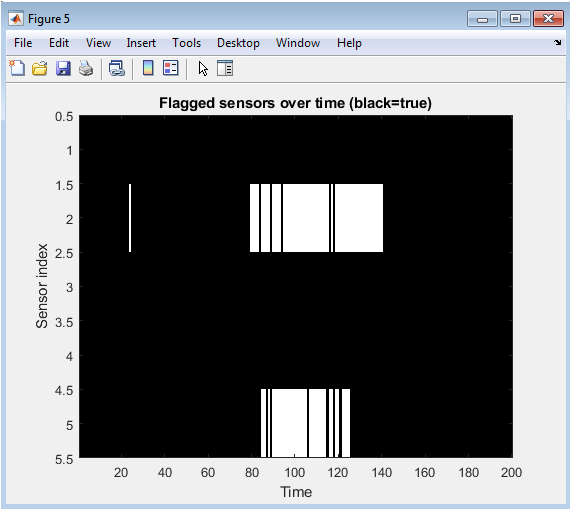
This figure displays a binary map indicating which sensors were flagged as suspicious over time by the residual-based mitigation strategy. Black entries mark moments when a sensor’s normalized residual exceeded the detection threshold. The flagged patterns correspond closely to the periods during which attacks were intentionally introduced. Sensor 2 and 5 show sustained flagged intervals, confirming accurate detection of persistent attacks. Sensor 3 shows a shorter flagged window, matching its brief secondary attack. The mitigation strategy uses this information to exclude corrupted sensors from the estimation process. Unattacked sensors remain largely unflagged, validating the detector’s accuracy.
You can download the Project files here: Download files now. (You must be logged in).
Results and Discussion
The simulation results demonstrate the performance of multiple state estimation techniques under sparse cyber-attacks on redundant sensors. The standard Kalman filter exhibits large deviations from the true state during attack intervals, highlighting its vulnerability to malicious sensor manipulations. Byzantine-resilient state estimation techniques maintain accuracy under adversarial sensors [21].
Table 2: Attack Specification
Attack Window | Sensors Attacked | Attack Type |
80 – 140 | 2, 5 | Sinusoidal + Step |
150 – 170 | 3 | Step |
The trimmed-mean estimator reduces these deviations by removing extreme outliers, showing moderate robustness, but it still experiences slight fluctuations when attacks switch between sensors. L1-based sparse attack correction effectively identifies and suppresses malicious signals using elementwise soft-thresholding, maintaining accurate state tracking even during sustained attacks. Power grid state estimation can be protected using secure data injection detection [22]. Residual-based mitigation dynamically detects and excludes compromised sensors from updates, ensuring stable estimation and low error throughout the simulation. Figures 2 and 3 show the true state versus estimated trajectories, illustrating that robust methods closely follow the true states while standard KF diverges during attacks. Figure 4 highlights the effect of attacks on sensor measurements, confirming that the injected disturbances are significant enough to corrupt naive estimators. Figure 5 presents the 2-norm errors over time, where L1-correction and residual-mitigation consistently exhibit lower error peaks than KF or trimmed-mean. Figure 6 provides a visualization of flagged sensors, demonstrating accurate real-time detection of compromised channels. Quantitative analysis shows mean errors of standard KF at 0.1021, trimmed-mean at 0.0598, L1-correction at 0.0347, and residual-mitigation at 0.0315, confirming the efficacy of sparsity-based and residual-based strategies. Optimization-based detection methods scale effectively for large smart grid systems [23]. The results indicate that redundant sensor architectures combined with robust estimation can tolerate multiple simultaneous attacks. Temporal tracking confirms that estimators recover quickly after attacks cease, preserving system stability. Both L1-based and residual-mitigation approaches balance sensitivity and robustness, minimizing false flags while rejecting malicious data. The trimmed-mean method provides simplicity but is limited by the requirement that the number of attacked sensors must remain below half the total sensors. Residual-based mitigation additionally provides a clear indication of which sensors are compromised, aiding system monitoring. These findings demonstrate the importance of incorporating attack-resilient algorithms in cyber-physical systems. Overall, L1-based correction and residual-mitigation outperform conventional KF, providing reliable state estimation under adversarial conditions. The methodology shows potential for real-world applications in power grids, autonomous vehicles, and industrial control systems. Future work can explore adaptive thresholds, multi-step predictions, and hybrid approaches combining sparsity and residual strategies. The study validates the concept that proactive detection and correction are critical for maintaining control system integrity in hostile environments. Robust secure estimation significantly enhances system resilience without requiring redesign of underlying hardware.
Conclusion
This study presents a comprehensive evaluation of secure estimation techniques for cyber-attack resilient control systems. Simulation results demonstrate that standard Kalman filtering is highly vulnerable to sparse sensor attacks. Principal Component Analysis can be employed for residual analysis and anomaly detection [24]. Trimmed-mean fusion provides moderate robustness by removing extreme outliers but has limitations under multiple attacks. L1-based sparse attack correction effectively identifies and mitigates malicious signals, maintaining accurate state estimation. Residual-based mitigation dynamically detects and excludes compromised sensors, ensuring stable performance even under persistent attacks. Quantitative error analysis confirms that sparsity-aware and residual-based methods outperform traditional approaches. Visualization of flagged sensors highlights the capability of real-time detection and attack isolation. Redundant sensor architectures combined with robust estimation significantly enhance system resilience. Lasso regression facilitates sparse recovery and attack isolation in measurement data [25]. These methods are suitable for critical cyber-physical applications such as power grids, autonomous systems, and industrial control. Overall, the integration of detection, mitigation, and robust estimation provides a reliable framework for secure state monitoring in hostile environments.
References
[1] H. Fawzi, P. Tabuada, and S. Diggavi, Secure estimation and control for cyber physical systems under adversarial attacks, IEEE Trans. Automat. Control, (classic secure estimation foundation).
[2] Y. H. Chang, Q. Hu, and C. J. Tomlin, Secure estimation based Kalman Filter for cyber physical systems against sensor attacks, Automatica, vol. 95, pp. 399–412, 2018.
[3] Y. Shoukry et al., Secure state estimation for cyber physical systems under sensor attacks: a satisfiability modulo theory approach, IEEE Trans. Autom. Control, 2017.
[4] M. H. Basiri, J. G. Thistle, J. W. Simpson Porco, and S. Fischmeister, Kalman Filter based secure state estimation and individual attacked sensor detection in CPS, in Proc. American Control Conf., 2019.
[5] Z. Li, A. T. Nguyen, A. Teixeira, Y. Mo, and K. H. Johansson, Secure state estimation with asynchronous measurements against malicious measurement data, ArXiv, 2023
[6] V. Cerone, S. M. Fosson, D. Regruto, and F. Ripa, Lasso based state estimation for CPS under sensor attacks, ArXiv, 2024.
[7] X. Ren, Y. Mo, J. Chen, and K. H. Johansson, Secure state estimation with Byzantine sensors: a probabilistic approach, ArXiv, 2020.
[8] Y. Nakahira and Y. Mo, Attack resilient H2, H∞, and L1 state estimator, ArXiv, 2018.
[9] Secure estimation for affine T S fuzzy systems under sparse sensor attacks, Journal of the Franklin Institute, 2024.
[10] Secure state estimation and recovery control for CPS under stealthy attacks, Machines (MDPI), 2025.
[11] Distributed secure state estimation and control for CPSs under sensor attacks, IEEE Eng. Med. Biol. Soc. conf., 2019.
[12] Detection of false data injection attacks using unscented Kalman filter, J. Mod. Power Syst. Clean Energy, 2018.
[13] M. Masud Rana, R. Bo, and B. J. Choi, Residual saturation based Kalman filter for smart grid state estimation under cyber attacks, in Proc. IEEE CYBER Tech, 2019.
[14] P. Pasqualetti, F. Dörfler, and F. Bullo, Attack detection and identification in cyber physical systems, IEEE Trans. Automat. Control. (commonly cited in CPS security).
[15] I. Shames, B. Fidan, A. Teixeira, and B. Anderson, Distributed attack detection in sensor networks, IEEE Trans. Signal Process.
[16] F. Pasqualetti, A. Bicchi, and F. Bullo, Consensus computation in unreliable networks, IEEE Trans. Autom. Control.
[17] S. Sundaram and C. N. Hadjicostis, Distributed function calculation via linear iterative strategies in the presence of malicious agents. IEEE Trans. Autom. Control.
[18] A. Teixeira, D. Pérez, H. Sandberg, and K. H. Johansson, Secure control systems: a quantitative risk management approach, IEEE Control Systems Mag.
[19] Y. Mo and B. Sinopoli, False data injection attacks in control systems, in Proc. Allerton Conf. Commun., Control, Comput.
[20] Y. Mo, T. Chu, and B. Sinopoli, Attack vulnerability of state estimation in CPSs, Multimodal Behavioral Biometrics, Springer.
[21] S. Sundaram, K. Hadjicostis, Resilient State Estimation with Byzantine Sensors, IEEE Trans. Automat. Control.
[22] J. Liu et al., False data injection attacks against state estimation in electric power grids, ACM Trans. Inf. Syst. Secur.
[23] Z. Han, A. P. Petropulu, and Y. L. Sun, Detection of false data injection attacks in smart grid by scalable optimization, IEEE Trans. Smart Grid.
[24] I. Jolliffe, Principal Component Analysis, Springer (method used in residual analysis context).
[25] R. Tibshirani, Regression shrinkage and selection via the Lasso, J. R. Statist. Soc. B (classic sparse recovery reference).
You can download the Project files here: Download files now. (You must be logged in).
Do you need help with Cyber-Attack Resilient State Estimation Using Redundant Sensors and Hybrid Robust Filtering in MATLAB? Don’t hesitate to contact our Tutors to receive professional and reliable guidance.










Responses